TL;DR
IHTeam undertook an independent security assessment of NextGen’s Mirth Connect version <= 4.3.0 and identified the following vulnerability:
- CVE-2023-37679 – Unauthenticated Remote Command Execution
What’s Mirth Connect
Mirth Connect (https://github.com/nextgenhealthcare/connect) is an opensource healthcare data integration system, that enables the management of information using bi-directional sending of many types of messages. The primary use of this interface engine is in healthcare.
CVE-2023-37679
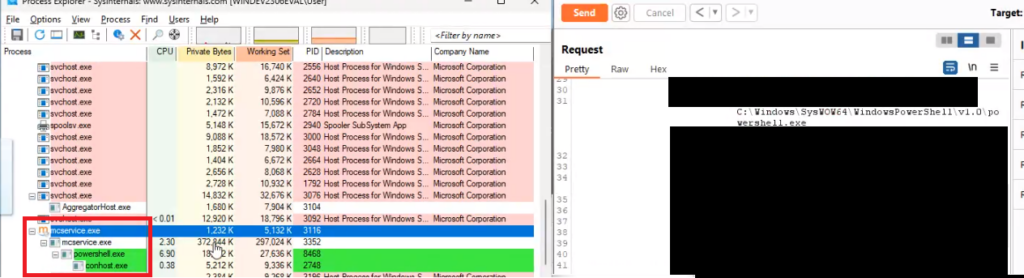
IHTeam identified a remote command execution on Mirth Connect <= 4.3.0 that can be exploited from an unauthenticated perspective. The only condition in which this CVE can be exploited is when JRE <= 8.0 is in use.
It should also be noted that, by default, the server starts with administrative privileges (root or SYSTEM), therefore the remote command execution will have a more serious impact.
The issue is affecting all version of the product (Linux, Windows and MacOS). The root cause was one of the internal servlet filters in the Mirth Connect’s code-base (not caused by any of the third-party components).
Version 4.4.0 resolved this issue and the vendor will soon stop supporting JRE 8.0 in favour of newer versions. Additional information can be consulted in the Changelog here: https://github.com/nextgenhealthcare/connect/wiki/4.4.0—What’s-New#remote-code-execution-vulnerability-when-using-java-8-and-elevated-permissions
Proof of Concept
The proof of concept request will never be released to avoid ransomware attacks on public healthcare systems. And also considering the fact that, although the management interface shouldn’t be exposed on the Internet, there are currently around 2000 systems in Shodan: https://www.shodan.io/search?query=title%3A%22Mirth+Connect+Administrator%22
Disclosure Timeline
21/06/2023 – Privately contacted NextGen’s security team at [email protected] with all technical details of the vulnerability
26/06/2023 – First response from NextGen
30/06/2023 – Beta version of 4.4.0 was shared and tested, confirming the fix for the reported vulnerability
31/07/2023 – Version 4.4.0 is publicly available on GitHub
02/08/2023 – This blogpost was published

2 replies on “Mirth Connect <= 4.3.0 Unauth RCE”
Will blocking ports 8080 and 8443 at the firewall mitigate the issue?
When will you be releasing the Proof of Concept?
Hi, I updated the article saying that a proof of concept will not be released to avoid ransomware attacks on public healthcare systems.
The management interface of Mirth-connect should never be exposed on the Internet in the first place, so place disable the port forwarding on the firewall.